Develop a robust information security strategy that evolves with your organization's present needs and future objectives, ensuring resilience and compliance.


Hiring a full-time Chief Information Security Officer (CISO) is costly and difficult due to the global cybersecurity talent shortage. At Benelec Infotech, our Virtual Chief Information Security Officer (V-CISO) Team Services offer expert security support without the high cost of in-house staff. Since 1995, we've helped businesses strengthen defenses, meet compliance needs, and stay ahead of cyber threats.
Guiding you through Annual Cyber Security Planning
Defining Cyber Security Strategy and Goals
Risk Assessment & Compliance Governance
Security Controls Implementation & Policy Definition
In today’s digital economy, information assets are the backbone of any organization. With increasing cyber threats and stringent regulations, securing your data is no longer optional—it's essential. Businesses must establish robust Information Security Management Systems (ISMS) to protect their valuable information from breaches, compliance risks, and operational disruptions.
ISMS Framework Implementation (ISO 27001)
Security Policies, Procedures & Documentation
Internal & External ISMS Audits
Incident Response & Risk Mitigation Strategies


In today’s data-driven world, safeguarding personal information is critical to both business success and trust. With rapidly evolving privacy laws like the DPDP Act, GDPR, and CCPA, organizations must comply with stringent regulations to protect sensitive data and avoid costly penalties. Ensuring compliance is not just about legal obligation—it’s about securing consumer trust, enhancing brand reputation, and mitigating privacy risks.
DPDP Act, GDPR, & CCPA Compliance
Data Privacy Framework Implementation (DPDP Act, GDPR, CCPA)
Data Subject Rights Management (Access, Erasure, Rectification, and Portability)
Privacy Policy & Procedure Development
Data Protection Impact Assessments (DPIAs)
Equip your team to recognize, prevent, and respond to cyber threats with confidence and clarity. Build a culture of security across your organization with engaging, practical training.
Cybersecurity threats evolve daily — empower your people with the knowledge and skills to stay ahead. From phishing to password hygiene, our training covers the most critical areas of digital safety.
Stay protected, stay informed — because your security is only as strong as your most unaware user.
Covers all key areas including phishing, malware, password protection, secure browsing, and social engineering – giving your team the tools they need to stay safe online
Designed for engagement with real-world examples, simulations, quizzes, and gamified learning paths to keep users involved and informed
Customizable content aligned to your industry, role-specific risks, and compliance requirements like DPDP Act,GDPR, HIPAA, or ISO standards
Training is not a one-time event – receive regular updates, monthly tips, and refresher modules to keep cybersecurity top of mind year-round
Fortify your digital infrastructure with expert-led security strategies and proactive defense mechanisms.
Identify, evaluate, and eliminate security loopholes before attackers can exploit them. Our VAPT services simulate real-world attacks to test your defenses, uncover vulnerabilities, and provide detailed remediation strategies.
We assess your internal and external network architecture to detect misconfigurations, insecure protocols, and unauthorized access points—ensuring your network is secure from the ground up.
Uncover security flaws in your applications through thorough code reviews and dynamic testing. We secure your apps against OWASP Top 10 threats and beyond.
Simulate targeted cyber attacks to evaluate your organization's detection and response capabilities. Our red team engagements go beyond VAPT to test your people, processes, and technologies under pressure.
Stay aligned with industry standards like ISO 27001, SOC 2, GDPR, and more. We provide in-depth audits, gap assessments, and documentation support for a seamless compliance journey.
Empower your workforce with cybersecurity best practices and role-specific training to build a culture of security within your organization.
Guiding You From Risk to Resilience.
Start with a no-obligation conversation to explore your IT environment. We’ll evaluate your current security setup and highlight any hidden threats that may be putting your data at risk.

Our specialists will break down the risks and craft a strategic security roadmap tailored to your business. This actionable plan is designed to strengthen weak points and align with your industry requirements.
We’ll bring your custom security strategy to life, implementing tools, policies, and protections with precision. You’ll benefit from real-time safeguards and continuous expert guidance—every step of the way.
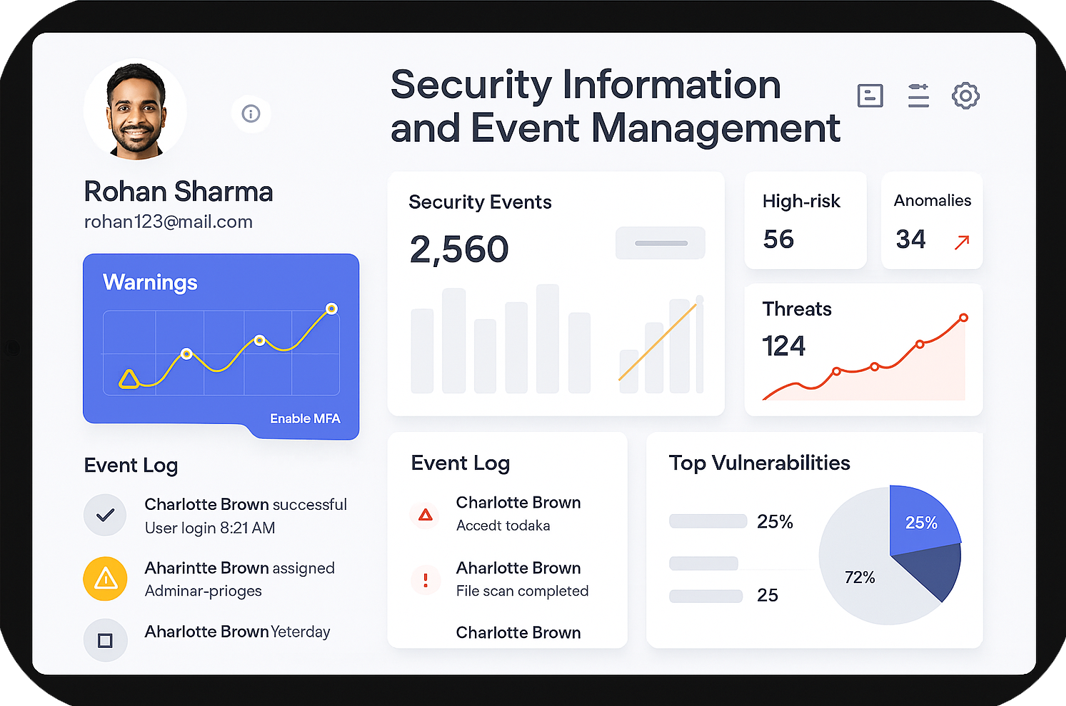
All security events are logged and stored for auditing and analysis. This enables you to review past events and identify trends or weaknesses in your security posture, helping you make informed decisions.
Each report not only provides a detailed overview of your security but also offers actionable insights to enhance your defense strategies. Use these insights to make informed decisions and strengthen your security framework.
Monitor all your systems from a single dashboard. View security events, vulnerabilities, and active threats in real-time, enabling you to make quick and informed decisions.